Objective : In this article we will try to understand roles , user life cycle and other concepts in OIM .
Terms often used within OIM .
User: It indicates OIM access.
Account : It indicates resource access . One user may have one or more accounts .
Roles : Roles are group of users who are doing similar job functions within an enterpirse . It may optionally have associated access.
Entitlements: It represents your privilege on the resources .To have an acces to entitlement user must have an accont on that resource .It represents what the user can do on the resource side . Entitlements are meant for target resources .
Admin Roles : These are privileges meant for administrating OIM . It represents what a user can do in OIM system . Admin roles will be assigned to OIM System Administrator. These are not the Business roles , IT roles , Enerprise roles , but are the privilegeswithin OIM system taht represents what a user can do within OIM system .
Application Instance : It is the combination of IT resource and a resource object . It is a provisionable entity . You need to
create one Application Instance so that it appears in catalog and user can request for it.In essence it represents a resource
within an enterprise.
Oracle Identity Manager User :
->User entity is data representation of a user .
->OIM manages to use minimum attributes to represent one user . Attributes such as login ID , describe user entity in Oracle Identity Manager environment .
->User is associated with a single user entity in Oracle Identity Manager environment . There will be only one user and any number of accounts associated with him. Every enterprise user must have access to OIM . All your business partners , employees , customers if they are accessing your resources then you must create one user within OIM for them and map all those accounts with the owner(OIM user ).
-> Administrator can manage the life cycle of user in OIM . Administrator can login and they can delete one user then OIM by
default deletes all his access from various resources . Also administrators can set the status of users within OIM . They can login and disable users , once they disable all their accounts get
disbale . For example lets say a female employee is going on maternity leave for 6 months . I dont want all her access to be Active So administrator will disable her account within OIM and all her accounts will also get disable . Administrators can also lack and unlock the account . All these thing are possible within OIM since OIM is the proxy administrator
or virtual administrator for all the resources within yur organization .
User Entity Life Cycle :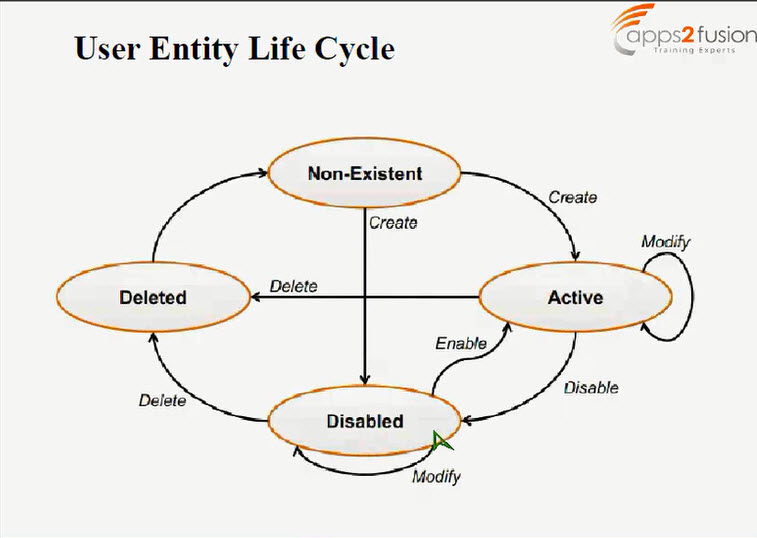
Non Existent State : Its the state when the user is not created .
Active State : When the user is created the user is in Active state . When its it Active state the user attributes can be modified .For example User is promoted to a new position. As a result, HR changes the job title of the user.
Also the user can be disbaled . When the user id disabled it moves to Disabled state , again the administartor can enable the user and it will go back to Active state .
Disabled State: When the user disbaled , its in Disbaled state .
Deleted State : From the Disabled state you can delete the user , & when the user is deleted it is in the Disabled state. Also when the user is in Active state it can be deleted .For example User retires from the company. HR manually deletes the user on the last working day of the user.
In OIM , even if you delete the user it doesnt get deleted from the database table, in the table it will just mark a flag that the user is deleted . The deleted user details will not be re-used by OIM . The user can also go into Disbale state as soon as its created when the administrator has set the effective date something different i.e not the same date as joining date . So if the effective date is after one month the user will be enabled after one month automatically .
Types of User :
End-User Administrator manages users , resources and organizations
End Users manage themselves.
System Administrator manage and customize Oracle Identity Manager .
End-User Administrator & End User ,they both login to identity self service console . If they are user administartors , if one of the admin role is assigned to them to create the new user , they will be able to create the user , delete the user and modify the user . If they are only end-users there will be no admin roles for them , they can modify only their profile and not of others .
System Administrators generally login to System Admin Console , for creating access policies , for setting password policies etc. and they will be having some admin roles so that they can manage the OIM System .
There is one more console known as Design Console ,it is typically used for mapping , development of forms , and developing a connector from scratch .
1.You need to run the launchDesignConsole.sh script in order to access the design console . 
2. It will ask you to enter credentials enter the OIM admin credentials.
3. It will prompt for changing the password
5. Your Design Console will appear
You can create roles , IT Resources Type Definition , Rul Designers , Resource Objects, which are used for developing a connector .
Oracle Identity Manager Roles:
->Roles gives users access right If users have similar access we create roles.Roles can be independent of an organization, span multiple organizations, or contain users from a single organization.Roles determine the links and menus that are available to users when they log in to the console.
->Associated with one or more access rights to Oracle Identity Manager functions.
->User should not be assigned with individual resources .Before assigning a role to user you need to find out the department to which the user belongs (HR,Accounts,IT , Project etc), based on that I will assign a role . Lets say we create a Project Manager role, and associate all applications a project manager need access to , with that role . So whenever any Project Manager joins we will directly make them the member of this Project Manager role andd the access associated with it will be granted. This type of methodology for provisioning the access is called as Role Based Access Control .
Two ways of role assignmnet :
1) User is directly assigned a role . All access rights associated with role are given to the user .End-Users can request themselves for a particular resource and based on the job code or any other attribute you can make them the member of a particular role automatically . We can write auto membership rule for a role .
2) Role is assigned to organization . User , when associates with the organization , inherits all role access rights .
-> Roles follow hierarchical strcuture 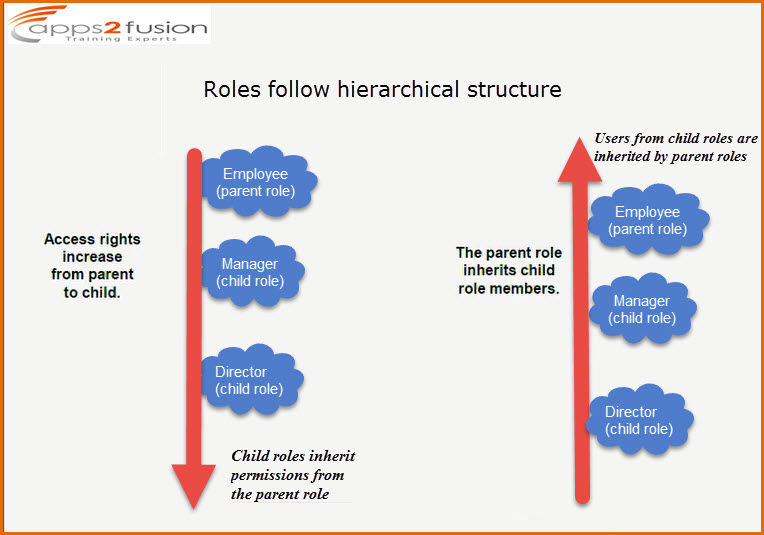
There are three roles here Employee(parent role) , Manager(child role of employee) and Director role which is child role of Manager.So Employees will be having access to lets say email , Managers will be having access to some Appraisal Application (self service app).Since Manager is child role of employee , managers will be having access to both Email application and self service app .Similarly if Director role which is the child role of Manager ,is assigned to the user , he will be porvisioned for the resources which are associated with the Director role , Manager Role as well as Employee Role since access rights increases from parent to child . Also the parent role inherits child role members . For example, for user1 I have assigned employee role , for user 2 I have assigned Manager role , and user 3 Director role. If you see the members of Director role you will see only user3, and if you see the memebrs of Manager role you will see user2 and user3 . If you see the members of Employee role , you will find all the three users user1 user2 & user3 .
We can take another scenario wherein we are implementing OIM for the first time and I need to load the users from various resources . For the first time I will consider AD1 and there will be a reconciliation job with the help of which we can pull the users from AD1 and save them in OIM . Lets say we could pull 500 users from AD1 . Once all the users are loaded in OIM , we will stop the AD1 reconciliation job . Suppose we have one more active directory AD2 from which we will search for few more users we can perform a reconciliation job for this as we did before . Lets say there 600 users in AD2 and few of these (say 200 ) users may already be there in AD1 . So what OIM does is it check each user account whether its already available in OIM or not(it can check employee id , email id or any other unique attributes ). For example it may search how many users are there with similar email id and link all those accounts to the owner if it finds . If the owner is not found in OIM it creates a owner . This is how a recon is configured for the second resource. In the recon we have an option to specify corelation rule . So this is an example of using recon to load the users .
-> A parent role can have multiple child roles .
-> A role may act both as a parent and child to other roles .
-> Child inherits parent's access rights .
-> Roles can be assigned to multiple users
-> A child role's member is a member of parent role .
Role Category :
Grouping of roles into a category . For example I can create category Finance and all the roles related to Finance can be grouped into Finance category.
Organization of roles for managing organizations
Default categories :
OIM Roles - Contains predefined roles
Default - Contains roles with no category.
Entity Relationships :
->User has one to one relationship with organization but one to many relationship with roles .
->Organization has one to many relationship with both users and roles
-> Role has many to many relationship with both organization and users .